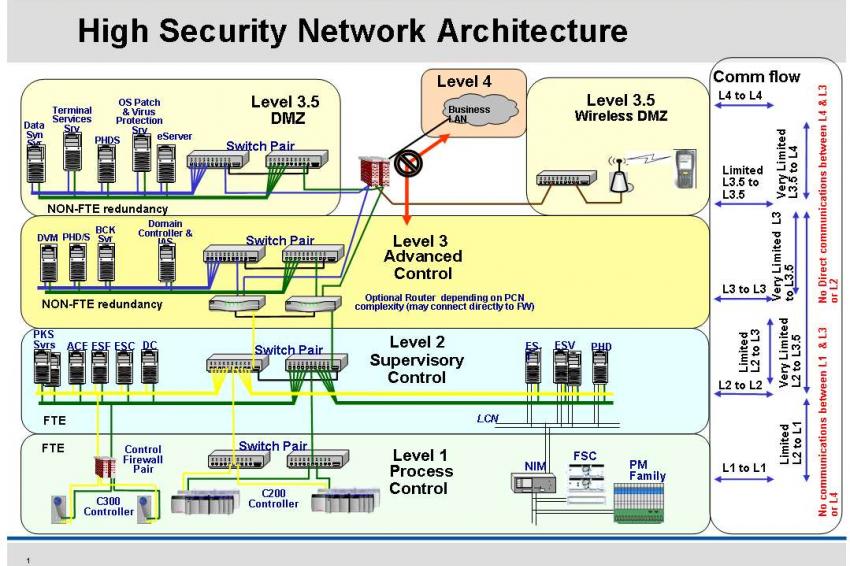
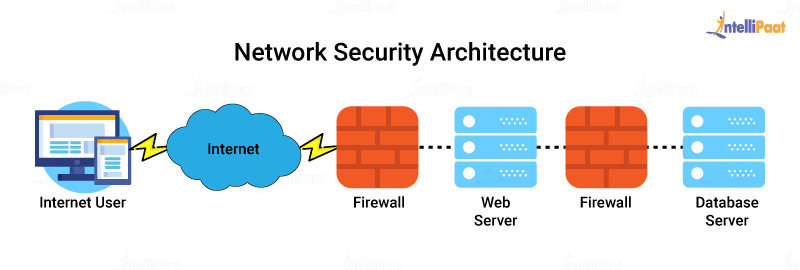
40 network security architecture diagram
LifeTime API Examples - OutSystems See some real-world scenarios of using a set of LifeTime API methods to perform common tasks like: Create a new application version; Deploy an application Understanding Network Access in Windows AppContainers ... Posted by James Forshaw, Project Zero Recently I've been delving into the inner workings of the Windows Firewall. This is interesting to me as it's used to enforce various restrictions such as whether AppContainer sandboxed applications can access the network. Being able to bypass network restrictions in AppContainer sandboxes is interesting as it expands the attack […]
security architecture and design 90 A+ Writers ... security architecture and design 90 A+ Writers | apluswriters.net. Hi, Need help with answers for attached questions. Figure 8.1 attached in document. 1.Minimum of 600 words. Assignment should be in APA format and have to include at least two references. Figure 8.1 Business analytics logical data flow diagram (DFD).
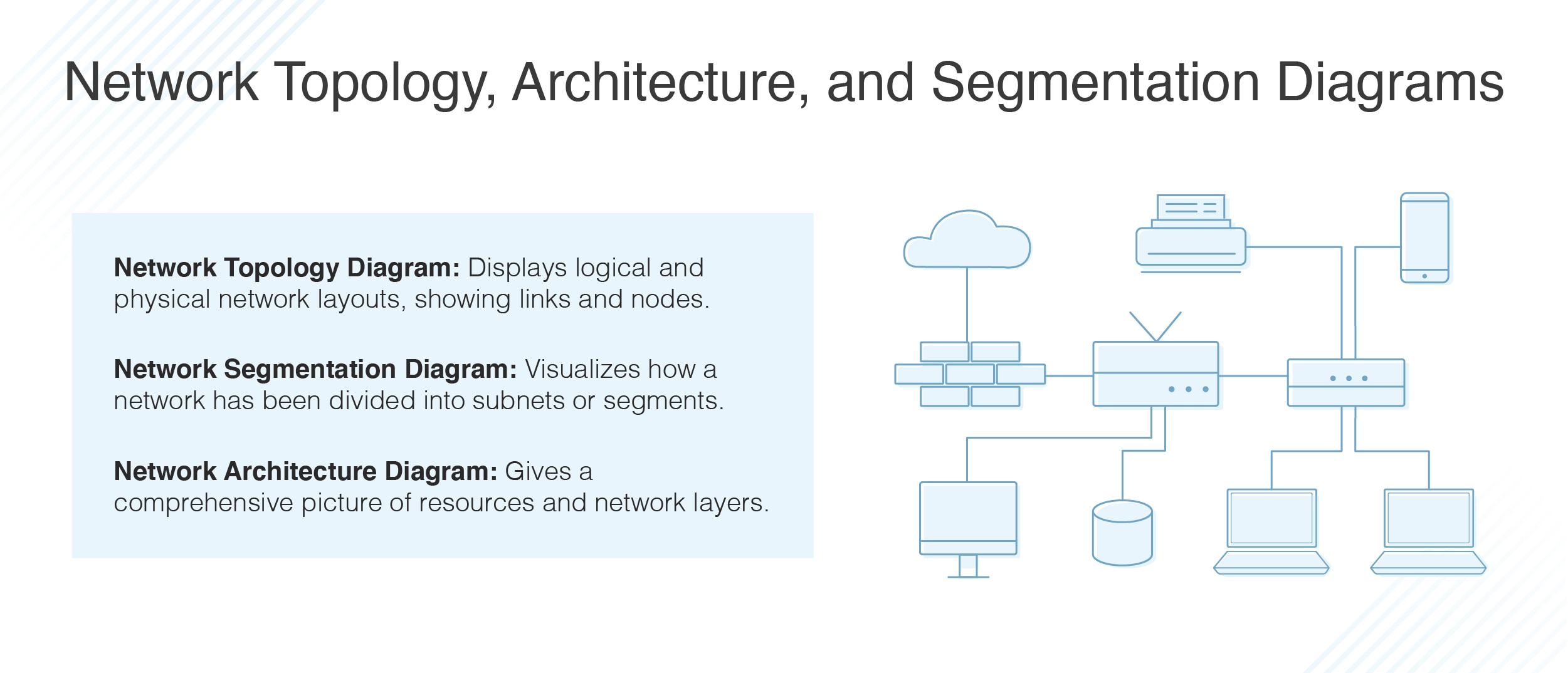
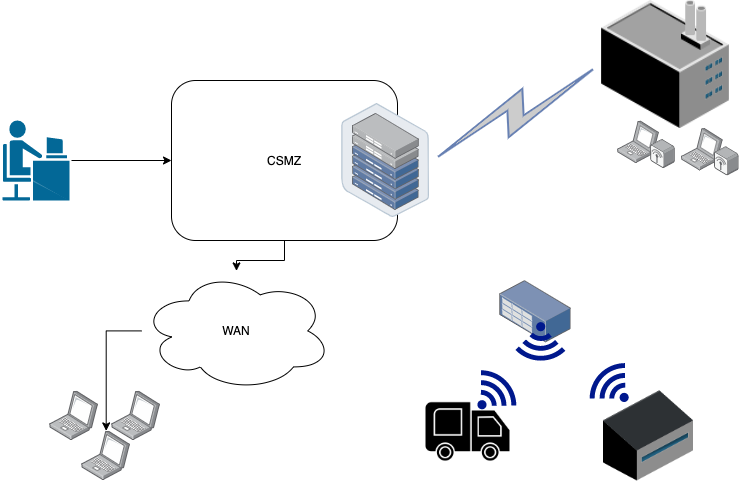
Network security architecture diagram
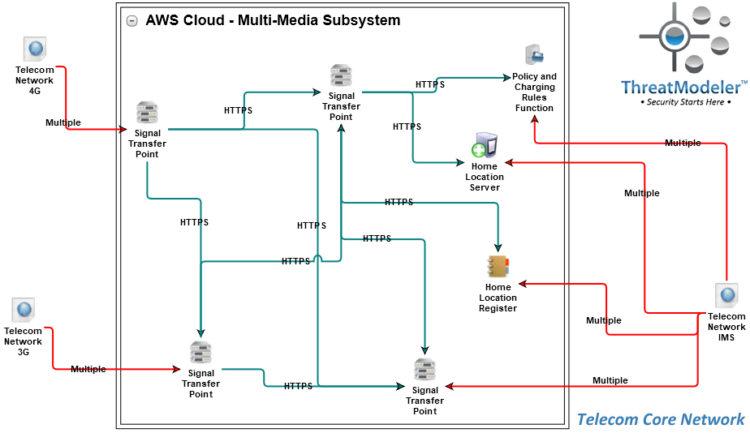
docs.aws.amazon.com › architectureThe AWS Security Reference Architecture - AWS Prescriptive ... Most architecture diagrams focus and dive deep on the web, application, and data tiers. For readability, they often omit the security controls. This diagram flips that emphasis to show security wherever possible, and keeps the application and data tiers as simple as necessary to show security features meaningfully. Infrastructure Architect, Cloud Platforms job in Mississauga, * Create the required artifacts (design document, diagrams, build book, etc..) ... network and/or security solution. * Applied Mature Architecture design framework, principles and methodologies (high-level technical design, low-level technical design, and technical solution design integration) ... KLM Careers Principal Network Security Architect - Tampa ... as the principal security architect (network) in cybersecurity services, you will be responsible for reviewing the existing network configuration (on-premises and cloud), proposing changes to existing control standards, crafting new it security standards, designing network security patterns & diagrams, and driving the network security capability …
Network security architecture diagram. Econometrics Answers Online 💸 🥇🎓 - essayhelpp.com The following production possibilities curve shows the tradeoff between housing and all other goods. a. If the current mix of […] Network Security Engineer II Job Lawrence Kansas USA,IT/Tech Participate in the development of viable and cost-effective security solutions. Propose new network designs based on the best and latest security practices. Communicate and maintain up-to-date, accurate documentation for passwords, diagrams, security, etc. Proactively plan for future security capacity and execute related action plans. Heuristics for Ukraine (and other places) - Chicago Boyz Heuristics for Ukraine (and other places) March 21, 2022 by Jay Manifold. NB: some of the following is from a recent videoconference that included our own Trent Telenko, who is very much the man of the hour, but some of it is more publicly available, not to mention common sense. First, though, as is my wont, a quadrant diagram to organize my ... Drones | Free Full-Text | Evaluation of a Multi-Mode ... Visibility and communication are the essential pillars for safe flight operations in dense airspaces. Small Unmanned Aerial Vehicles (UAVs) of the order of up to 25 kg are increasingly being used at airports as a cost-effective alternative for maintenance and calibration work. However, the joint operation of manned and unmanned aircraft in busy airspaces poses a major challenge. Due to the ...
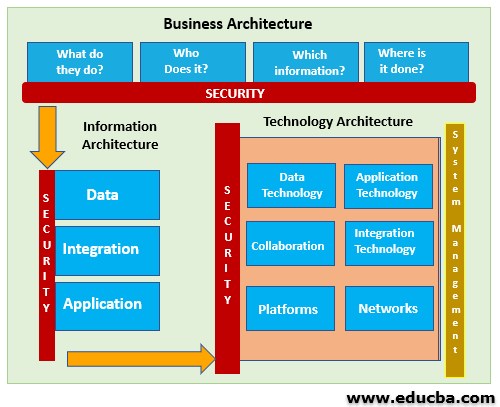
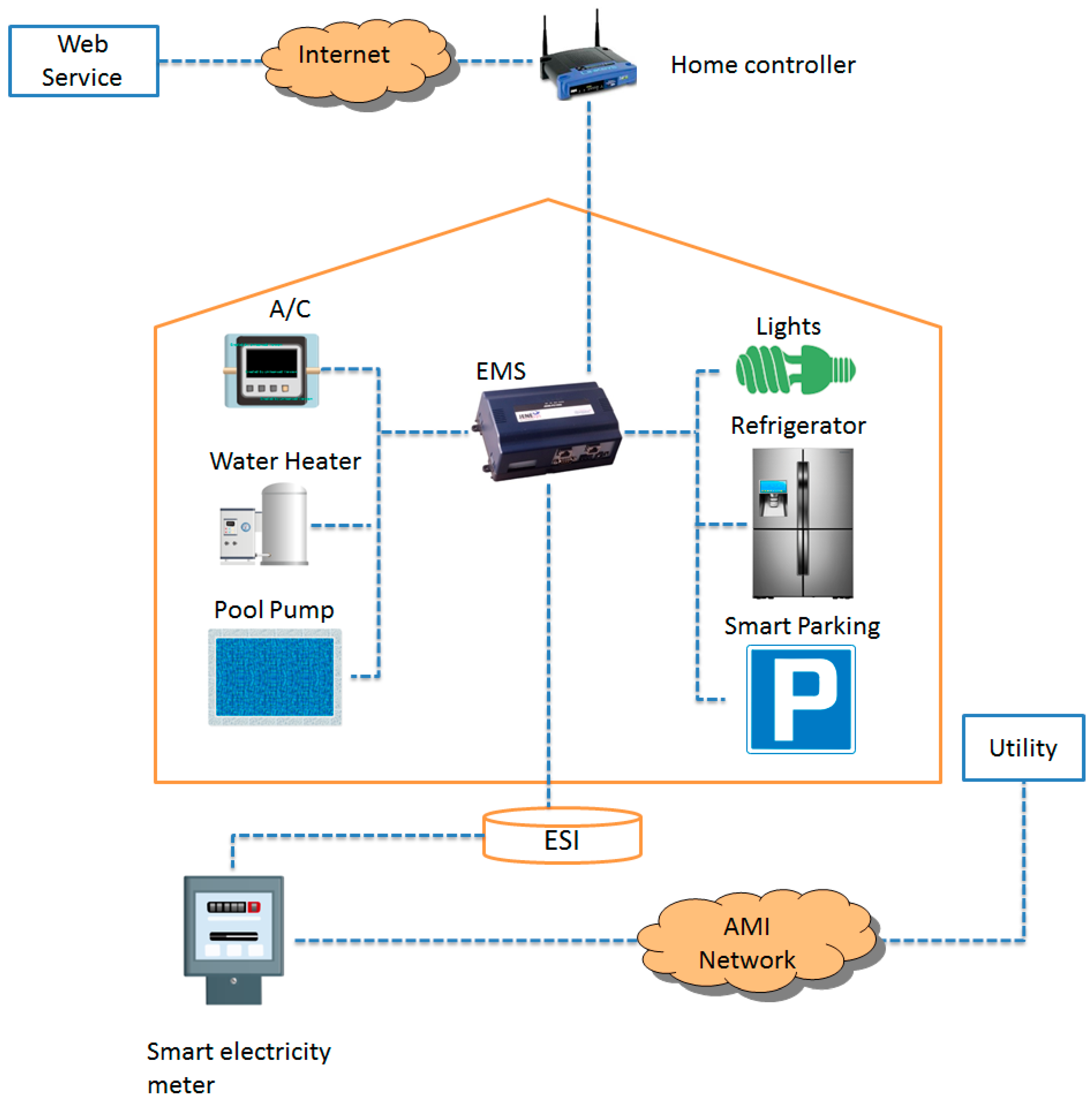
Digital personalized healthcare web archive collection and ... Because C/S architecture is a point-to-point structure pattern in which the server and the client are paired together, it adopts a network protocol with good security, so it has high security. It has fast execution speed. Because the C/S architecture's business logic is processed on the client side, the results are then submitted to the server. intellipaat.com › blog › cloud-computing-architectureCloud Computing Architecture with Diagram - Intellipaat Mar 12, 2022 · Cloud Computing Architecture. Cloud Architecture in Cloud Computing, is a combination of several components and subcomponents that form together. Cloud Computing security architecture is categorized into frontend and backend, along with an amalgamation of the event-driven architecture and the service-oriented architecture in Cloud Computing. CWRU PAT Coffee Agenda - patcoffee.phys.case.edu We use the TNG100 simulation of the IllustrisTNG project to investigate the stellar specific angular momenta ($j_{\ast}$) of $\sim$12~000 central galaxies at $z=0$ in ... main page main page. Next; 22.03.2022 by bedub Leave a Comment by bedub Leave a Comment
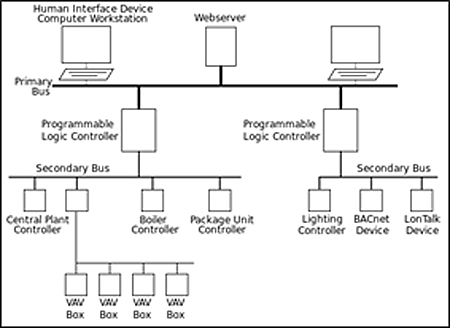
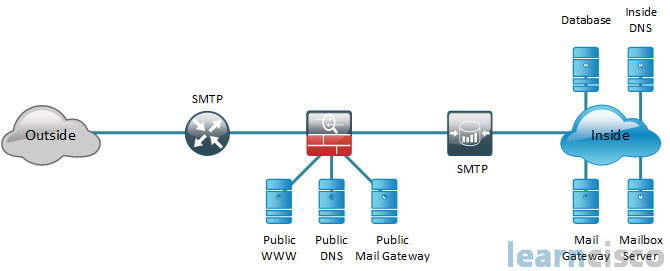
A Deep Learning Framework for Image Authentication: An ... The main aim of digital image forensics is to validate the authenticity of images by identifying the camera that captured the image and finding traces of any alteration in the spatial content. The majority of the existing literature focuses on manual extraction of intrinsic camera features such as lens aberration, sensor imperfections, pixel non-uniformity, color filter array type, and so on ... System One Senior Network Engineer in Washington, DC ... Strong understanding of network architecture and application development methodologies Design and deploy functional networks (LAN, WLAN, WAN) Monitor network performance and integrity Automate tasks and monitor their effectiveness Maintain complete technical documentation using C4 Model nomenclature and diagrams Suggest improvements to network ... Bolivia - Wikipedia Bolivia, officially the Plurinational State of Bolivia, is a landlocked country located in western-central South America. The constitutional capital is Sucre, while the seat of government and executive capital is La Paz.The largest city and principal industrial center is Santa Cruz de la Sierra, located on the Llanos Orientales (tropical lowlands), a mostly flat region in the east of the country. › network-diagram-examplesNetwork Diagram Examples | Free Download | EdrawMax Sep 27, 2021 · The diagram is the physical network diagram that represents the IT components that are connected with each other by cables, which is also shown. Many IT professionals, industries, network administrators, cybersecurity experts use the diagram as a roadmap for their networks.
› aws-architecture-diagramAWS Architecture Diagram: A Complete Tutorial | EdrawMax AWS architecture diagram is the diagrammatic representation of the application that is completely cloud-native means it is completely hosted on the AWS platform.. The diagram can also be of the application that is not hosted on the cloud but using some of the services provided by the AWS like the databases, or cache, etc.
Principal Network Security Architect Job Dallas Texas USA ... as the principal security architect (network) in cybersecurity services, you will be responsible for reviewing the existing network configuration (on-premise and cloud), proposing changes to existing control standards, crafting new it security standards, designing network security patterns & diagrams, and driving the network security capability …
Aws Stencils For Omnigraffle - diagrameasy.com The official AWS icon set for building architecture diagrams. While most drawing tools are designed for use on one operating system ConceptDraw DIAGRAM is available as. Ad 人気商品がお買い得価格で登場Amazon Primeなら対象商品は配送料無料 数億種の品揃え amazoncojp has been visited by 1M users in the past month.
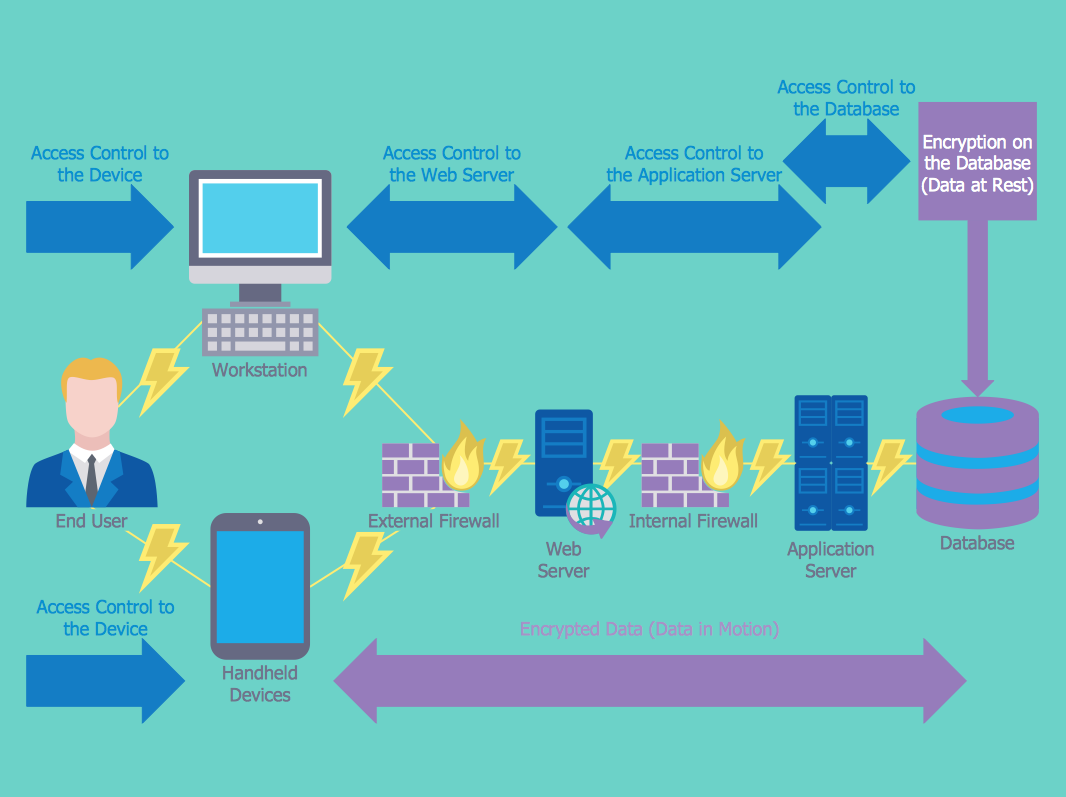
IT System Security Engineer Job Reston Virginia USA,IT/Tech IT System Security Engineer. Duration: 06 months contract to hire. Location: Reston, Virginia. Position Description. Design, prototype and support security-related infrastructure and applications. Identify and mitigate security risks to network and systems. Architect, develop and engineer enterprise security tools which may be COTS ce.
Retail Network Engineer at Levi Strauss & Co | JobEka.lk Excellent network systems documentation and architecture diagram skills Strong verbal and written communication skills are necessary due to the dynamic nature of collaborations with customers, vendors, and other engineering team, solving complex business problems together.
Qumodity Network Security Engineer in Smithfield, RI ...
Incident response 3 | Computer Science homework help ... Your task is to assist in analyzing and documenting the incident described below. The Blue Team has already created a set of enterprise architecture diagrams (see figures 1-4) to help with your analysis of the incident and preparation of the incident report as required by the company's contracts with the federal government.
Principal Security Architect - IAM Job Coppell Texas USA ... Principal Security Architect - IAMFull-time, Onsite 40%Dallas, TX, Tampa, FLOur client, a global leader in the Financial Services industry, is seeking a Principal IAM Security Architect to conduct a comprehensive review of existing identity access management controls (on-premise and cloud), influence change in the controls standards, create IT security standards easily ...
KLM Careers Principal Network Security Architect - Tampa ... as the principal security architect (network) in cybersecurity services, you will be responsible for reviewing the existing network configuration (on-premises and cloud), proposing changes to existing control standards, crafting new it security standards, designing network security patterns & diagrams, and driving the network security capability …
Infrastructure Architect, Cloud Platforms job in Mississauga, * Create the required artifacts (design document, diagrams, build book, etc..) ... network and/or security solution. * Applied Mature Architecture design framework, principles and methodologies (high-level technical design, low-level technical design, and technical solution design integration) ...
docs.aws.amazon.com › architectureThe AWS Security Reference Architecture - AWS Prescriptive ... Most architecture diagrams focus and dive deep on the web, application, and data tiers. For readability, they often omit the security controls. This diagram flips that emphasis to show security wherever possible, and keeps the application and data tiers as simple as necessary to show security features meaningfully.























0 Response to "40 network security architecture diagram"
Post a Comment